Product Overview
Product Overview
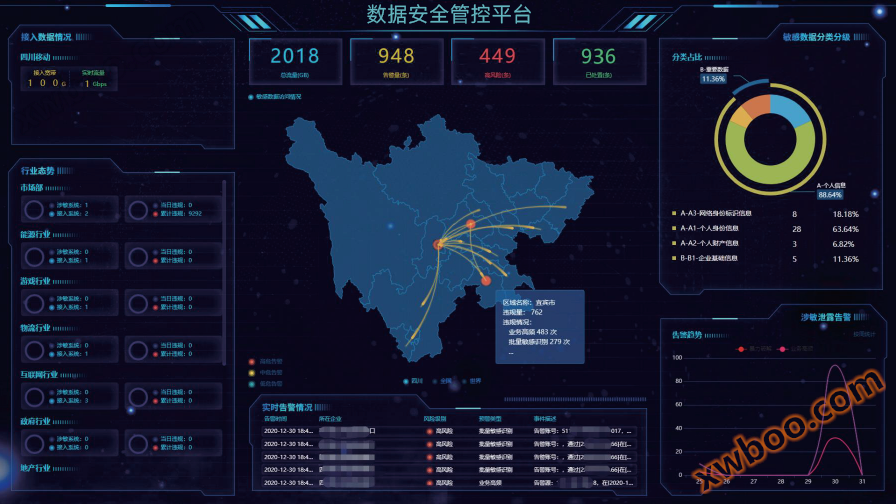
The data security management and control platform is mainly aimed at the enterprise Internet data import and export traffic. Through multi protocol traffic collection and analysis, it continues to improve the identification and analysis capabilities, follows the latest domestic and industry standards for data security, and focuses on the ability characteristics such as fitting the industry data flow life cycle, to promote the construction of the data security supervision system for sensitive and important data of government and enterprise units in the massive Internet access relationship. The platform emphasizes the ability to expand loose coupling, standardize strategy design, flexibly deploy software and hardware, and integrate operation and maintenance engineering, adapting to changing market demands and technological requirements trends.
The data security control platform includes asset mapping subsystem, data security monitoring subsystem, and data security operation subsystem. By collecting data security analysis results of various atomic capabilities, we provide professional data security capabilities for various operational tasks such as unified management, analysis, judgment, warning, and situational analysis.
 Features
Features
 Access analysis:It supports data traffic access in various Internet networks, office networks, production networks, public cloud, private cloud environments, such as bypass, PCAP, Agent, etc; Simultaneously achieve content parsing and formatting restoration for multiple types of general, database, and other protocol traffic.
Access analysis:It supports data traffic access in various Internet networks, office networks, production networks, public cloud, private cloud environments, such as bypass, PCAP, Agent, etc; Simultaneously achieve content parsing and formatting restoration for multiple types of general, database, and other protocol traffic.
 Data recognition:Provide data recognition, file recognition, interface recognition, path recognition, analysis and completion of asset supervision and data classification and grading traffic log information for parsing and restoring traffic.
Data recognition:Provide data recognition, file recognition, interface recognition, path recognition, analysis and completion of asset supervision and data classification and grading traffic log information for parsing and restoring traffic.
 Asset discovery:Provide enterprises with automatic discovery and coordinated management of resources including business systems, WEB data assets, interface assets, database sites, download sites, etc.
Asset discovery:Provide enterprises with automatic discovery and coordinated management of resources including business systems, WEB data assets, interface assets, database sites, download sites, etc.
 Risk monitoring:Based on enterprise data assets and sensitive transmission network traffic logs, provide risk alerts for protection vulnerabilities caused by system design defects and various data leakage events caused by abnormal access source behavior.
Risk monitoring:Based on enterprise data assets and sensitive transmission network traffic logs, provide risk alerts for protection vulnerabilities caused by system design defects and various data leakage events caused by abnormal access source behavior.
 Statistical analysis:Based on asset and monitoring data, construct statistical analysis models such as multi view, multi angle, and multi role event tracing, pathway identification, correlation analysis, line tracing analysis, and data flow maps.
Statistical analysis:Based on asset and monitoring data, construct statistical analysis models such as multi view, multi angle, and multi role event tracing, pathway identification, correlation analysis, line tracing analysis, and data flow maps.
 Traceability and evidence collection:Based on data security standards and enterprise requirements, in the process of identifying and tracing security incidents, provide formatted and unformatted forensic information files to ensure the ability to trace incidents.
Traceability and evidence collection:Based on data security standards and enterprise requirements, in the process of identifying and tracing security incidents, provide formatted and unformatted forensic information files to ensure the ability to trace incidents.
 典型部署
典型部署